Initial Server Setup
- (if it's a reinstall) remove server from known_hosts in .ssh folder
Create a new user and Grant access
It is not a good practice to use the root account apart from the initial server setup, so we create a new user, and give it appropriate access.
adduser newUser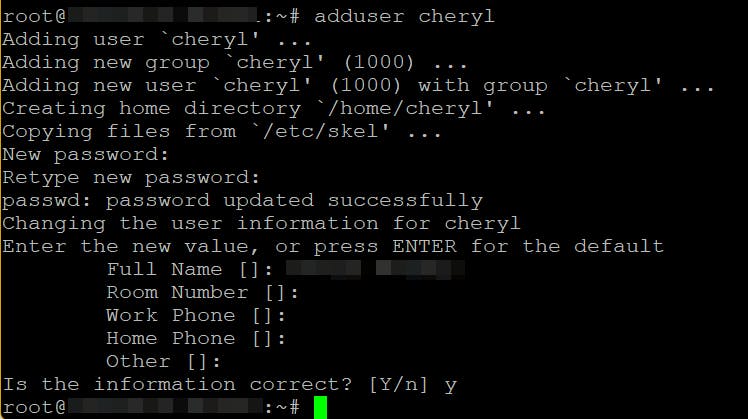
Update package repositories
apt update apt upgrade -y- (if sudo is not installed) Install sudo, and add the new user to the sudo group.
newUser is then put into the sudo group which members are allowed to use the sudo command in Debian
apt install sudo -y usermod -aG sudo newUser Setup firewall (ufw)
apt install ufwcheck available profiles using the following command
ufw app listOpenSSH should be on the list. It should come preinstalled on Debian 10. If not, check out Enable SSH Server on Debian 11
Then, allow traffic to and from OpenSSH
ufw allow OpenSSHEnable the firewall
ufw enablecheck the firewall status
ufw status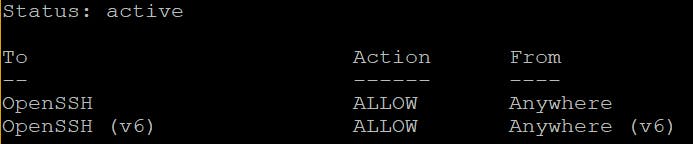 This confirms the firewall is on and allowing traffic to and from OpenSSH
This confirms the firewall is on and allowing traffic to and from OpenSSH(Optional) Top 8 Things to do after Installing Debian 10 (Buster)
(Optional) Setup SSH
Generate the key pair on the client (your computer) In windows powershell
ssh-keygen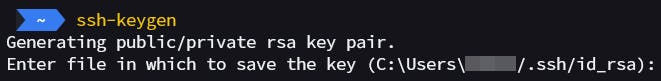 Specify path and filename (.ssh in the home directory and id_rsa is the default path and filename respectively)
Specify path and filename (.ssh in the home directory and id_rsa is the default path and filename respectively)Enter a passphrase (highly recommended for security). If a passphrase is set, you'll be required to enter this for authentication.
 Now the key pair is generated and saved in the directory specified.
Now the key pair is generated and saved in the directory specified.Copy the public key (the generated file with .pub extension) to the server
In Windows Powershell, if /.ssh directory already exist in the user home directory. use this command to copy the public key to the server, replacing the filename, username, and server IP.
cat ~/.ssh/key-filename.pub | ssh newUser@123.45.6.7 "cat >> ~/.ssh/authorized_keys"Otherwise, if .ssh directory does not already exist, use the following
cat ~/.ssh/key-filename.pub | ssh newUser@123.45.6.7 "mkdir ~/.ssh; cat >> ~/.ssh/authorized_keys"Enter 'yes' to "Are you sure you want to continue connecting?" and the user password to continue.
If everything is setup correctly, we should be able to SSH into the server using the follow command. Enter the pass phrase set up earlier
ssh newUser@123.45.6.7 -p 22 -i ~/.ssh/<filename>- (optional) To connect to the server without having to specify the identity file every time, edit /.ssh/config, add the following entry for the VPS. Using the same username, VPS IP and filename used above. "Host" can be anything descriptive
Host 123.45.6.7 (newUser) HostName 123.45.6.7 User newUser IdentityFile ~/.ssh/<filename>ssh newUser@123.45.6.7
Setup the Web Server (Nginx)
Remember to Reload Nginx
sudo systemctl reload nginx
(Optional) Setup SSL
This is optional unless your TLD requires it, such as .dev
Let's Encrypt provides SSL certificate which lasts 3 months and can be set to automatically renewed using the certbot package.
Add Subdomains
- Create a new directory like /var/www/subdomain.mydomain.dev/html
Make a new file, subdomain.mydomain.dev in /etc/nginx/sites-available, with the following content
server { listen 80; listen [::]:80; root /var/www/mydomain/html; index index.html index.htm index.nginx-debian.html; server_name mydomain www.mydomain; location / { try_files $uri $uri/ =404; } }Create symbolic link in sites-enabled
sudo ln -s /etc/nginx/sites-available/subdomain.mydomain.dev /etc/nginx/sites-enabled/Add SSL Certificates with certbot We have to redo all the old and new domains and subdomains.
sudo certbot --nginx -d mydomain.dev -d www.mydomain.dev -d subdomain.mydomain.dev -d subdomain2.mydomain.devRestart nginx
sudo systemctl reload nginx